SAZKA SMShing Attack [EN]
Caught in the Easter Trap
![SAZKA SMShing Attack [EN] SAZKA SMShing Attack [EN]](/images/4/7/5/7/c/4757c327cf9eaa772cb3677e82e3bbb786766a78-banner.png)
I recently came across a fairly well-made SMShing attack where the attackers faithfully mimicked the website of SAZKA, a Czech company mainly running number games and betting. The attackers took advantage of the company's advertising campaign promoting limited Easter scratch tickets and targeted the company's customers.
In this attack, the attackers sent an SMS message to the victim's phone containing a link to a website. In SMS victim was offered a free lottery ticket to celebrate Easter and the arrival of spring with a top prize of up to 2 million CZK, which is a classic baiting technique used by attackers to lure victims into clicking on links.

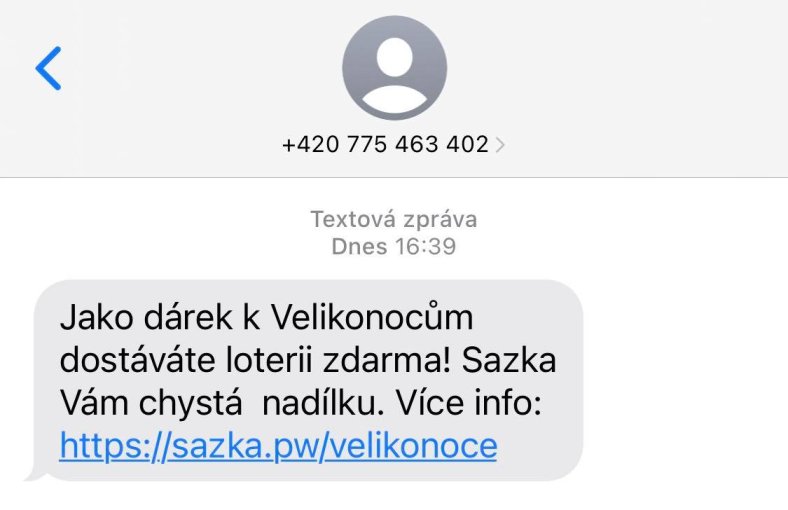
Once the victim clicked on the link, they were taken to a website that looked just like the legitimate SAZKA's website. The attackers were able to copy the website faithfully, which made it difficult for the victim to distinguish between the real and fake site. They even registered the look-alike domain sazka[.]pw.

However, most of the links on the site led either to a fake payment gateway or a form requesting sensitive data such as an address. The fake payment gateway demanded payment of 1 CZK.


What makes this attack even more interesting is that after the victim entered their card details, the fraudulent payment confirmation page was shown and asked for a confirmation code, which could come to the victim, for example, in a text message to their mobile phone. If the victim was using a code sent via SMS to confirm payments, attackers would be able to bypass this second payment confirmation factor.


Overall, this SMShing attack is an excellent example of how attackers are becoming more sophisticated in their techniques to deceive victims into divulging sensitive information. It is also an interesting coincidence that the victim who received the SMShing is indeed actively using the SAZKA websites. It is important to be aware of these types of attacks and to take precautions to protect your personal and financial information and verify the legitimacy of a website before accessing it or entering any data.



![Random Security News [CZ] Random Security News [CZ]](/images/f/9/e/6/0/f9e607b5573ed22609f53d567cd9a6e0bc065c32-internet-security.webp)

![LEGO Facebook Scam [EN] LEGO Facebook Scam [EN]](/images/f/5/2/3/c/f523c8411877effaa05a15f73ed8cf5de3a07473-legoheader.png)
![Random Security News [CZ] Random Security News [CZ]](/images/f/0/e/2/1/f0e218aedf4b8a6f9fb82df33b72891117f394de-internet-security.webp)
![LEGO Facebook Scam [EN] LEGO Facebook Scam [EN]](/images/9/5/8/8/8/95888f0e6396e4d4be8ec7a82755e778c40a2646-legoheader.png)
![SAZKA SMShing Attack [EN] SAZKA SMShing Attack [EN]](/images/b/9/a/6/e/b9a6ec564c74de29d94bd55b18580218f894cc15-banner.png)